X-LAB: Securing the Future of Telecom Networks
Discover the Future of Telecom Security
Welcome to X-LAB—your gateway to advanced telecom security testing and compliance. From simulated 4G/LTE, 5G NSA/SA, and ORAN environments to vulnerability detection and compliance validation, we empower telco operators, vendors, and security providers to innovate, secure, and accelerate their solutions.
Telecom Security Lab
Whether you are securing telco workloads, pitching advanced solutions, or ensuring compliance, Xecurity Pulse Security Labs provide the ideal platform to achieve your goals. Empower your team, validate your technology, and lead the way in telecom security innovation.
Why Choose X-LAB?

Simulated Telco Environments:
- Realistic 4G/LTE, 5G NSA/SA, and ORAN setups.
- Cutting-edge security tools for testing real-world scenarios.

Advanced Security Testing
- Identify vulnerabilities and audit configurations.
- Interactive demos for step-by-step insights.

Compliance & Benchmark Reporting
- Align with 3GPP, GSMA, and privacy standards.
- Generate security certifications and detailed reports.
Who Can Benefit?
Telco Operators:
Validate and enhance your network’s security readiness against evolving threats.
Vendors
Audit and benchmark your solutions to demonstrate robust security capabilities.
Innovators:
Test and refine your offerings in a real-world simulated environment before deployment.
Use cases - For Telecom Operators (MNOs):
- Test the resilience of network workloads against emerging threats using simulated exploits.
- Strengthen your security posture by identifying and fixing misconfigurations.
- Ensure compliance with local and global regulations, including GDPR and telecom-specific privacy laws.
- Validate your network’s adherence to 3GPP/GSMA standards.
- Certify vendor solutions against benchmarked security requirements before deployment.
- Enhance confidence in vendor offerings to reduce deployment risks.
- Simulate breach scenarios to test and refine incident response protocols.
- Train teams on handling real-world security events effectively.
- Test your products in a real-world simulated environment to identify vulnerabilities.
- Gain insights into improving the security of network functions and software solutions.
- Generate benchmark reports to demonstrate security strengths to telecom operators.
- Stand out by showcasing validated, high-security products during pitches.
- Ensure that your offerings meet global security compliance frameworks and data privacy requirements.
- Validate solutions faster with pre-built compliance and security frameworks, accelerating time to market.


Who Can Benefit?

Telco Operators:
Strengthen network security against threats.

Vendors:
Showcase security capabilities and achieve certifications.

Innovators:
Optimize products in real-world simulations.

Security Professionals:
Gain hands-on experience in telecom security.
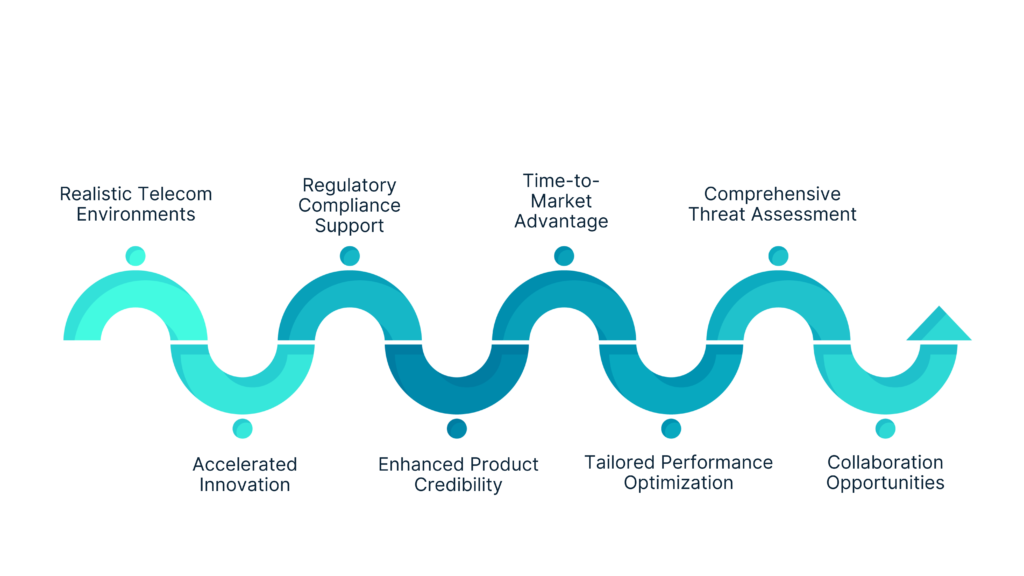
Key Use Cases

Threat Mitigation & Security Hardening
- Simulate attacks and reinforce network defenses.
- Resolve misconfigurations to strengthen security posture.

Compliance Validation
- Verify adherence to GDPR, 3GPP, and GSMA standards.
- Ensure privacy compliance across telecom networks.

Vendor Certification & Go-to-Market Acceleration
- Benchmark products and validate compliance.
- Reduce risks and speed up deployment timelines.

Incident Response Planning
- Simulate breaches and test response strategies.
- Train teams to handle real-world security events effectively.
Who Can Benefit?
Telco Operators:
Validate and enhance your network’s security readiness against evolving threats.
Vendors
Audit and benchmark your solutions to demonstrate robust security capabilities.
Innovators:
Test and refine your offerings in a real-world simulated environment before deployment.
Use cases - For Telecom Operators (MNOs):
- Test the resilience of network workloads against emerging threats using simulated exploits.
- Strengthen your security posture by identifying and fixing misconfigurations.
- Ensure compliance with local and global regulations, including GDPR and telecom-specific privacy laws.
- Validate your network’s adherence to 3GPP/GSMA standards.
- Certify vendor solutions against benchmarked security requirements before deployment.
- Enhance confidence in vendor offerings to reduce deployment risks.
- Simulate breach scenarios to test and refine incident response protocols.
- Train teams on handling real-world security events effectively.
- Test your products in a real-world simulated environment to identify vulnerabilities.
- Gain insights into improving the security of network functions and software solutions.
- Generate benchmark reports to demonstrate security strengths to telecom operators.
- Stand out by showcasing validated, high-security products during pitches.
- Ensure that your offerings meet global security compliance frameworks and data privacy requirements.
- Validate solutions faster with pre-built compliance and security frameworks, accelerating time to market.
Benefits of Using X-LAB
Interactive Features:

Virtual Tours:
Explore the lab with interactive maps and walkthroughs.

Architecture Diagrams:
Highlight lab setups and security components.

Hands-On Demos:
Experience simulated attacks and mitigation strategies.
Take the Next Step in Telecom Security!
Join the leaders in telecom security testing. Explore X-LAB’s tools, interactive demos, and real-world simulations.